Caddy: Manual Maintenance Mode
Coming from NGINX and others the concept of a maintenance mode that can be manually enabled is something I have used many times before.
With Caddy it is equally as easy, just using a less obvious syntax.
[Read More]HaProxy: Think About DNS Resolution
By default HAProxy resolves all DNS names in it’s config on startup and then never again.
This might cause issues down the road if DNS records, for example the ones for backends, change.
This section of the documentation is a good starting point as it describes IP address resolution using DNS in HAProy really well: https://docs.haproxy.org/3.0/configuration.html#5.3
Additionally this guide can also be helpful: https://www.haproxy.com/documentation/haproxy-configuration-tutorials/dns-resolution/
Self-hosted notifications
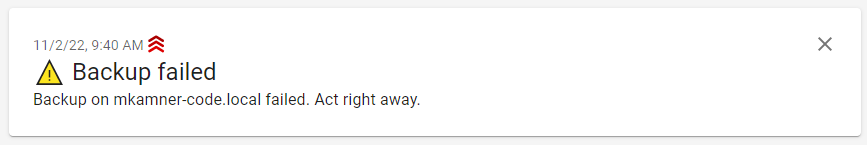
Running any kind of personal infrastructure sometimes requires your attention based on certain events or failure states, no matter how much you automate tasks.
Over the years I have used E-Mail, Telegram bots and a variety of other tools for this purpose. However all of them have the drawback that they mix with other kinds of information and are not easilly usable in scripts.
[Read More]Resolve .local Through Nameserver With Netplan
When using netplan it is easy to force .local DNS requests to go to you nameservers instead of being only resolved locally (the default and standard).
This also works with all other strange .WHATEVER domains you may have lying around in your organization.
Snippet from netplan configuration:
nameservers:
addresses:
- X
- Y
search:
- local
- myotherstupiddomain
Show all active user cron jobs on a system
Debian/Ubuntu
grep -vH "#" /var/spool/cron/crontabs/*
RedHat/Centos/Rocky
grep -vH "#" /var/spool/cron/*
DNS Resolution Everywhere
curl: Modify DNS Resolution
How SELinux screws with scripts when run over VMware Tools
SELinux by default prohibits certain things from working through VMware tools (Ansible connection or plain API).
This can be solved two ways:
- Disabling SELinux: BAD, but easy
- Writing a custom SELinux policy: complicated but more secure
Note: Adding/Changing this policy through a VMware tools connection is thankfully possible
Example policy
This policy is the base for a VMware tools policy and allows entering the rpm context (yum).
module custom-vmtools 1.0;
require {
type rpm_script_t;
type vmtools_unconfined_t;
class process transition;
}
#============= vmtools_unconfined_t ==============
allow vmtools_unconfined_t rpm_script_t:process transition